1. Disable not charging Popups
sudo defaults write com.apple.usbd NoIPadNotifications \-bool YES
sudo defaults write com.apple.usbd NoIPhoneNotifications \-bool YES
2. Creating a read only .dmg from a folder
hdiutil create ~/Desktop/newimage.dmg -volname "MyVolume" -srcfolder ~/Desktop/myfolder
3. Pairing Records
Pairing records are the crypto keys used by the pc to talk to the device. They are stored on the mac on /var/db/lockdown. If they are copied to other machines, you will not have to click trust every time.
4. Interesting Files on Devices iOS 7 & 8
/private/var/root/Library/Caches/locationd/cache_encryptedA.db
/private/var/root/Library/Caches/locationd/cache_encryptedC.db
/private/var/root/Library/Caches/locationd/lockCache_encryptedA.db
/var/preferences/SystemConfiguration/com.apple.wifi.plist
/private/var/wireless/Library/CallHistory/call_history.db
5. Device Out of Space?
One possible source of your space bing consumes is Crash logs. You can use your favorite method to remove remove the logs.
One more strange location of collecting files is:
/private/var/mobile/Library/Caches/com.apple.springboard.sharedimagecache/Persistent
SpringBoard related .cpbitmap files may start to collect here
Not if there are a ton of file in the directory, try the following command to remove them
echo SBUIControlCenterButton._backgroundImageWithGlyphImage.bg_<optional add file numbers here>* | xargs rm
6. Reflash iOS Device Procedure [TOP SECRET]
6.1 - Functional Device
Generally the phones used for development work have NO classified data stored on them, but they have been connected to a classified developer network, so the phone must be inspected and cleaned of any classified information. Most mobile devices support reduced functionality modes for firmware restoration. This reduces the likelihood of information leakage.
- Clear the phone of classified information by:
- Removing all data files (if any) from phone,
- Deleting all traces of development activity (proceses, development code, etc),
- Deleting all crash logs,
- And checking the phone for an option to either "Delete all user data" or "Restore to Factory Condition" and running it.
- Get someone else with access to the classified network (DEVLAN) to inspect the device for the above.
- Log the phone's inventory or serial number, date, your name, name of verifier, etc on DEVLAN
- This phone is TEMPORARILY approved for connection to the unclassified network (the Internet) for updating the firmware or operating system, activation, rooting or jailbreak, and configuration.
- Connect to the Internet (using existing USB connection, or WiFi, or cellular) in recovery/restore mode.
- Complete all necessary activities.
- The device is no longer approved for connection to the unclassified network (Internet). Return it to the classified network (DEVLAN).
6.2 - NON-Functional Device
If the phone is non-functional then you cannot directly delete any possible classified data. If possible, re-flash the entire firmware with an old (any) version of the operating system on the classified network (DEVLAN). Re-flashing will overwrite all stored data.
- Re-flash the phone operating system
-
See Reflash iOS Device for instructions specific to iOS devices (iPhones, iPads, and iPods) -
Device Firmware Update (DFU) Mode- Put the device into DFU mode by:
- Power off the device
- Connect the device to the activation station via USB
- While the device is off, hold both the power and home button for ten (10) seconds
- Release the power button, but keep pressing the home button
- The screen will not turn on while in DFU mode until the process is complete.
Update the Firmware
- Once the device has been scrubbed or put into DFU mode, it can be updated/restored to the current firmware.
- Put the device into DFU mode
- Press and hold the home button and the power button simultaneously.
- Wait ten seconds.
- While maintaining the home button depressed, release the power button
- Wait ten more seconds.
- Release the home button
- Wait for iTunes to prompt you to restore the device and hold the option key while clicking the button. This will prompt you to pick a firmware file to load onto the device.
- Select the file that matches the hardware version (all boxes should be labeled with the hardware version, firmware version, and firmware build number)
Record on the box the new firmware version and build number.
-
Get someone else with access to the classified network (DEVLAN) to inspect the device for the above.
-
Log the phone's inventory or serial number, date, your name, name of verifier, etc on DEVLAN
-
This phone is TEMPORARILY approved for connection to the unclassified network (the Internet) for updating the firmware or operating system, activation, rooting or jailbreak, and configuration.
-
Connect to the Internet (using existing USB connection, or WiFi, or cellular) in recovery/restore mode.
-
Complete all necessary activities.
-
The device is no longer approved for connection to the unclassified network (Internet). Return it to the classified network (DEVLAN).
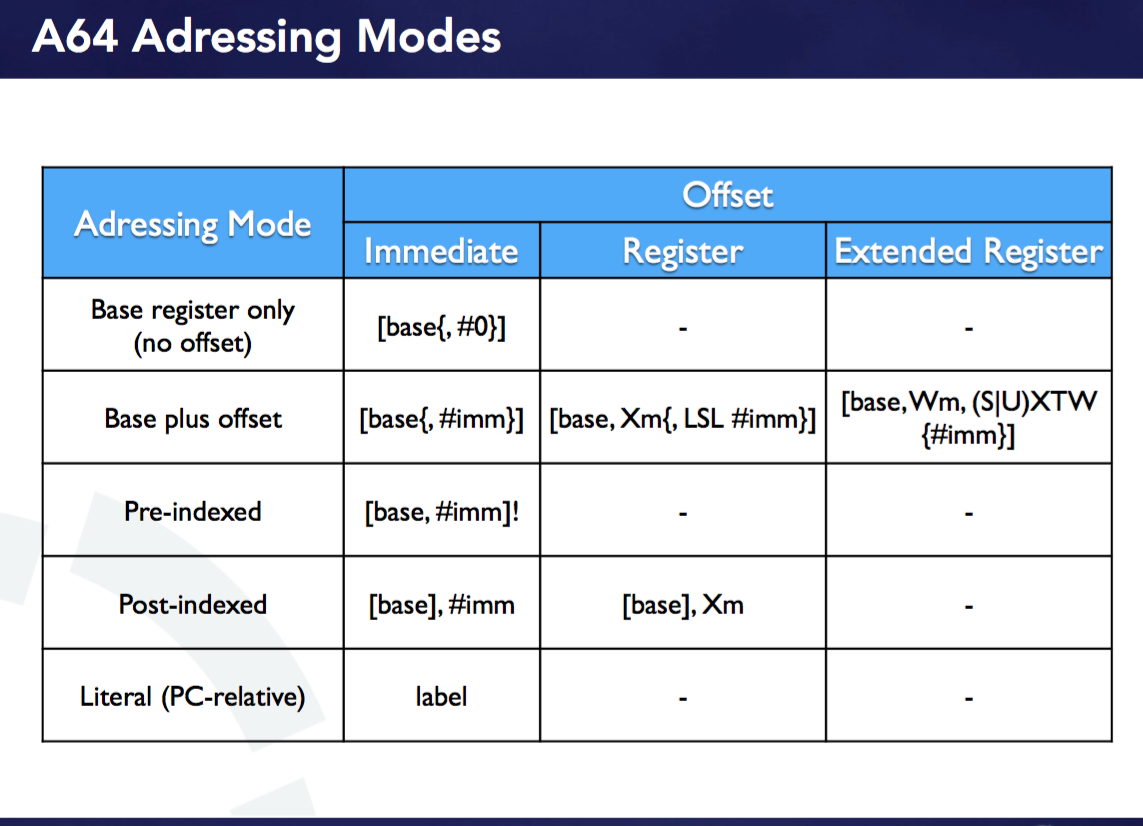
7. ARM64 Addressing Modes
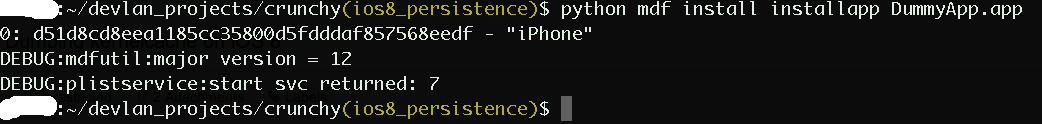
8. Installing an application using the commandline
- Provision a device.
- Build the app (using the debug configuration if RE-REDUXing).
- Using the mdf project, upload the application using:
python mdf afc transfer <path to the .app directory on your local machine, i.e. ~/myproject/Build/Products/.../myapp.app). this uploads the .app to the/var/mobile/Media/PublicStagingdirectory
python mdf install installapp <appname>. This moves the app from/var/mobile/Media/PublicStaging/myapp.appto the right directory.- Application should be installed and its icon shown on Springboard.
Eaxmple
1. Build, copy path to signed application

2. Transfer application

3. Install application
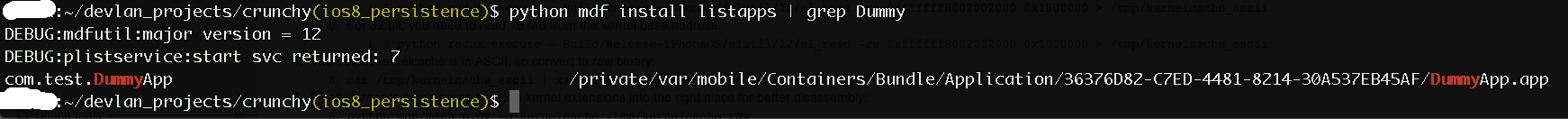
9. Displaying the list of Xcode environment variables.
These are accessible a script in a build phase.
xcodebuild -project machinjection.xcodeproj -target "machinjection" -showBuildSettings
10. FauxPas
Application that inspects an Xcode project and warns about possible bugs, as well as maintainability and style issues.

11. Lockdownd
Lockdownd is a daemon on the device that provides services for interacting with an iOS device. Some of these services include:
| Service Name | Description |
|---|---|
| afc | Apple File Conduit, used by iTunes to exchange files(mostly Media, like photos and videos) between the device |
| syslog_relay | System Log Relay, used by Xcode to display the syslog from the device. You can see this in action in Xcode by going to menu `Window -> Devices` 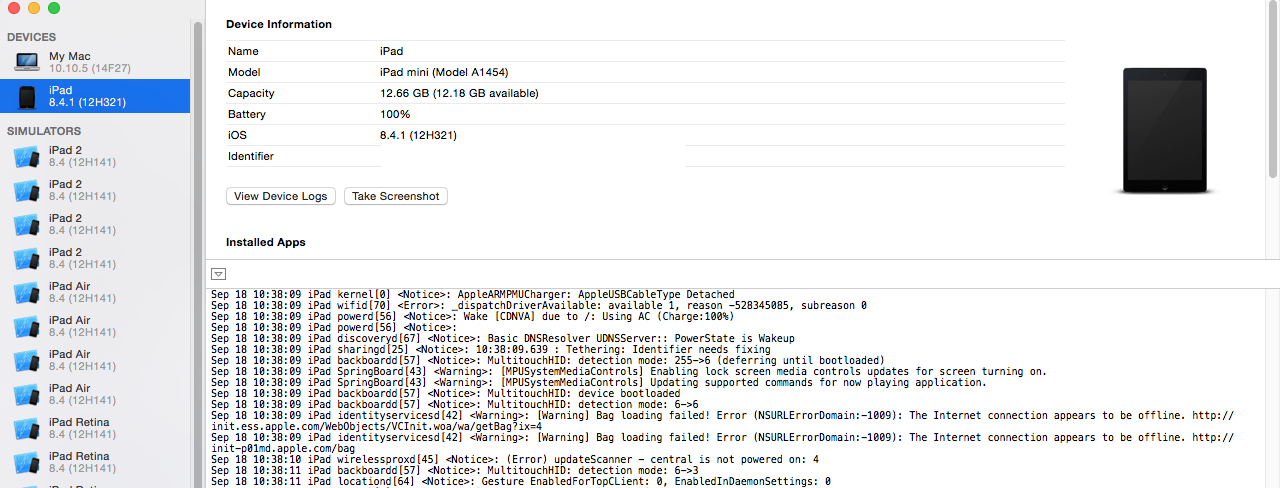 |
| diagnostics_relay | Retrieves device information, as well as power-related functions like sleeping, restarting, and shutdown. See https://github.com/Cykey/ios-reversed-headers/blob/master/MobileGestalt/MobileGestalt.h for various keys you can use to retrieve device information. |
Read more at WikiLeaks